Site-to-site IPsec VPN with two FortiGate devices
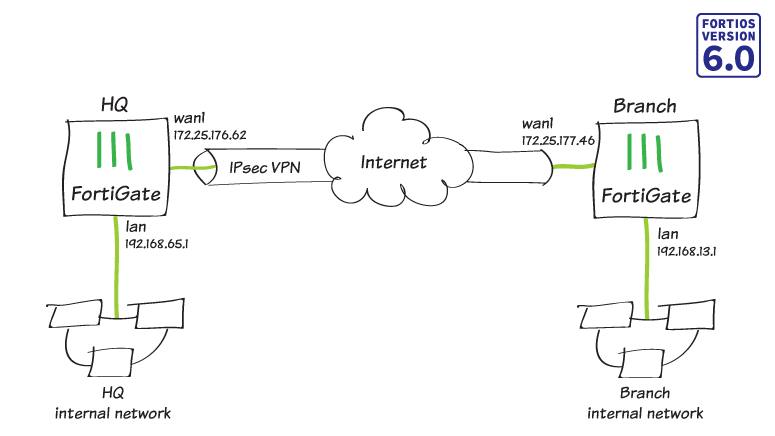
In this recipe, you create a site-to-site IPsec VPN tunnel to allow communication between two networks that are located behind different FortiGate devices. You use the VPN Wizard’s Site to Site – FortiGate template to create the VPN tunnel on both FortiGate devices.
In this example, one FortiGate is called HQ and the other is called Branch.
Configuring IPsec VPN on HQ
- To create a new IPsec VPN tunnel, connect to HQ, go to VPN > IPsec Wizard, and create a new tunnel.
- In the VPN Setup step, set Template Type to Site to Site, set Remote Device Type to FortiGate, and set NAT Configuration to No NAT between sites.

- In the Authentication step, set IP Address to the public IP address of the Branch FortiGate (in the example, 172.25.177.46).
- After you enter the IP address, the wizard automatically assigns an interface as the Outgoing Interface. If you want to use a different interface, select it from the drop-down menu.
- Set a secure Pre-shared Key.

- In the Policy & Routing step, set Local Interface to lan. The wizard adds the local subnet automatically. Set Remote Subnets to the Branch network’s subnet (in the example, 192.168.13.0/24).
- Set Internet Access to None.

- A summary page shows the configuration created by the wizard, including interfaces, firewall addresses, routes, and policies.

- To view the VPN interface created by the wizard, go to Network > Interfaces.

- To view the firewall addresses created by the wizard, go to Policy & Objects > Addresses.

- To view the routes created by the wizard, go to Network > Static Routes.

- To view the policies created by the wizard, go to Policy & Objects > IPv4 Policy.

Configuring IPsec VPN on Branch
- To create a new IPsec VPN tunnel, connect to Branch, go to VPN > IPsec Wizard, and create a new tunnel.
- In the VPN Setup step, set Template Type to Site to Site, set Remote Device Type to FortiGate, and set NAT Configuration to No NAT between sites.

- In the Authentication step, set IP Address to the public IP address of the HQ FortiGate (in the example, 172.25.176.62).
- After you enter the IP address, the wizard automatically assigns an interface as the Outgoing Interface. If you want to use a different interface, select it from the drop-down menu.
- Set the secure Pre-shared Key that was used for the VPN on HQ.

- In the Policy & Routing step, set Local Interface to lan. The wizard adds the local subnet automatically. Set Remote Subnets to the HQ network’s subnet (in the example, 192.168.65.0/24).
- Set Internet Access to None.

- A summary page shows the configuration created by the wizard, including interfaces, firewall addresses, routes, and policies.

- To bring the VPN tunnel up, go to Monitor > IPsec Monitor. Right-click under Status and select Bring Up.

Results
Users on the HQ internal network can access resources on the Branch internal network and vice versa.
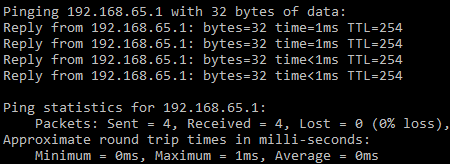
To test the connection, ping HQ’s LAN interface from a device on the Branch internal network.
Comments
Post a Comment
If you any doubt , Please let me know